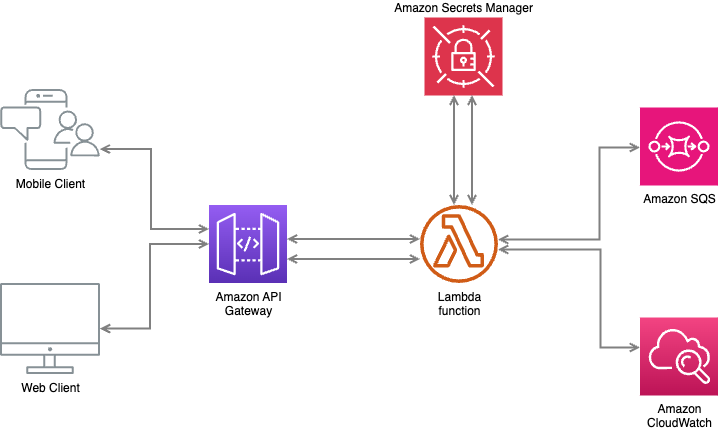
Secure Secrets Management on AWS SAM with AWS Secrets Manager
In the ever-evolving landscape of cloud computing, where data security reigns supreme, the management of sensitive information holds the key to a robust and resilient infrastructure. AWS Secrets Manager comes in handy as a crucial guardian of digital assets by providing a secure vault for managing access credentials, API keys, and other critical information on AWS. In this blog, we’ll uncover the significance of AWS Secrets Manager, delving into its pivotal role in secure credential management and seamless integration with…